Cloud Security- A Deeper Dive into Cloud Computing
Data is shifting to the cloud at a record pace and businesses, organizations are moving more and more workloads to the cloud. On the another side, some organizations continue resistant to the cloud’s significant attractions due to surviving interests about the data security. When approving Cloud Computing, it is important to assume and recognize the challenges of data protection in the cloud.
What is Cloud Security?
Cloud computing security is set of technologies, policies, applications that involve protecting analytical information from theft, data leakage and deletion. Our topmost priority is to give our customers a seamless service with massive value through building of security services. At a user level your data is guarded under Data Centers, but there are some countries that need data to be stored in their country only, so they want a provider that has various data centers all over the world so can manage data security.
How Do You Manage Security In The Cloud?
Cloud service providers use various methods to protect data.
Firewalls are a pillar of Cloud system. Firewall guards the outer edge of network security and end users.
Access Controls is technique that accomplished who or what can view or use resources in computing architecture. The main purpose of access control is to overcome the risk of unauthorized access to the physical and logical systems. By keeping strict access control, we can easily manage our analytical documents from hackers and malicious insiders with stolen credentials.
Data Masking is a security technique that protects the sensitive data from users. This maintains data fidelity by holding critical information private. The aim is to protect actual data while having a useful substitute for an instance when the real data is not required. In data masking the data may be changed in various ways i.e. character substitution, character shuffling but the data values must be changed in the way that it makes detection.
Threat Intelligence As name itself suggest, it helps you to preserve critical information from threats. The threat intelligence market, an industry which is reviled to recompense more than $13bn by 2025. That has comes up with a key specialties such as business reliability, data integrity, customer trust etc.
Disaster recovery It is a solution to security that helps you to recover the data that has been lost or stolen. In simple terms, it is a backup and recovers strategy that includes managing and storing copies of electronic records in cloud computing architecture as a security standard.
Cloud security challenges
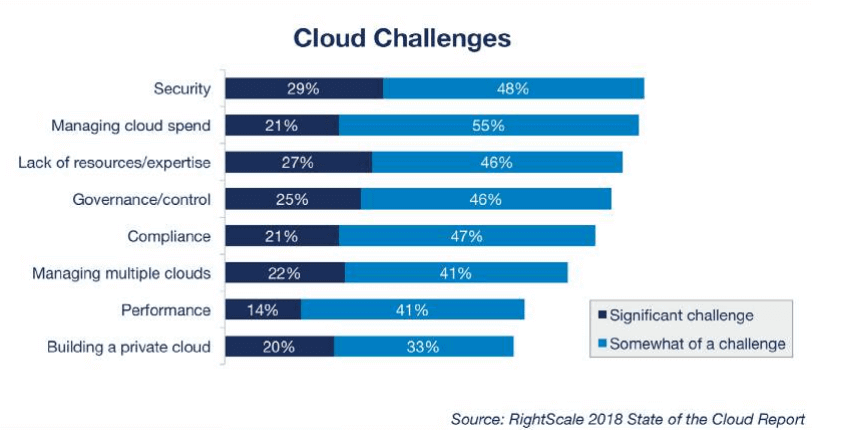
In spite of having certain benefits of Cloud integration, only 33% of companies have positive attitude toward adopting the Cloud. According to the survey of IT security leaders by Cloud Security Alliance (CSA) it introduces some effects that holds you back to the cloud adoption, starting with some common challenges:
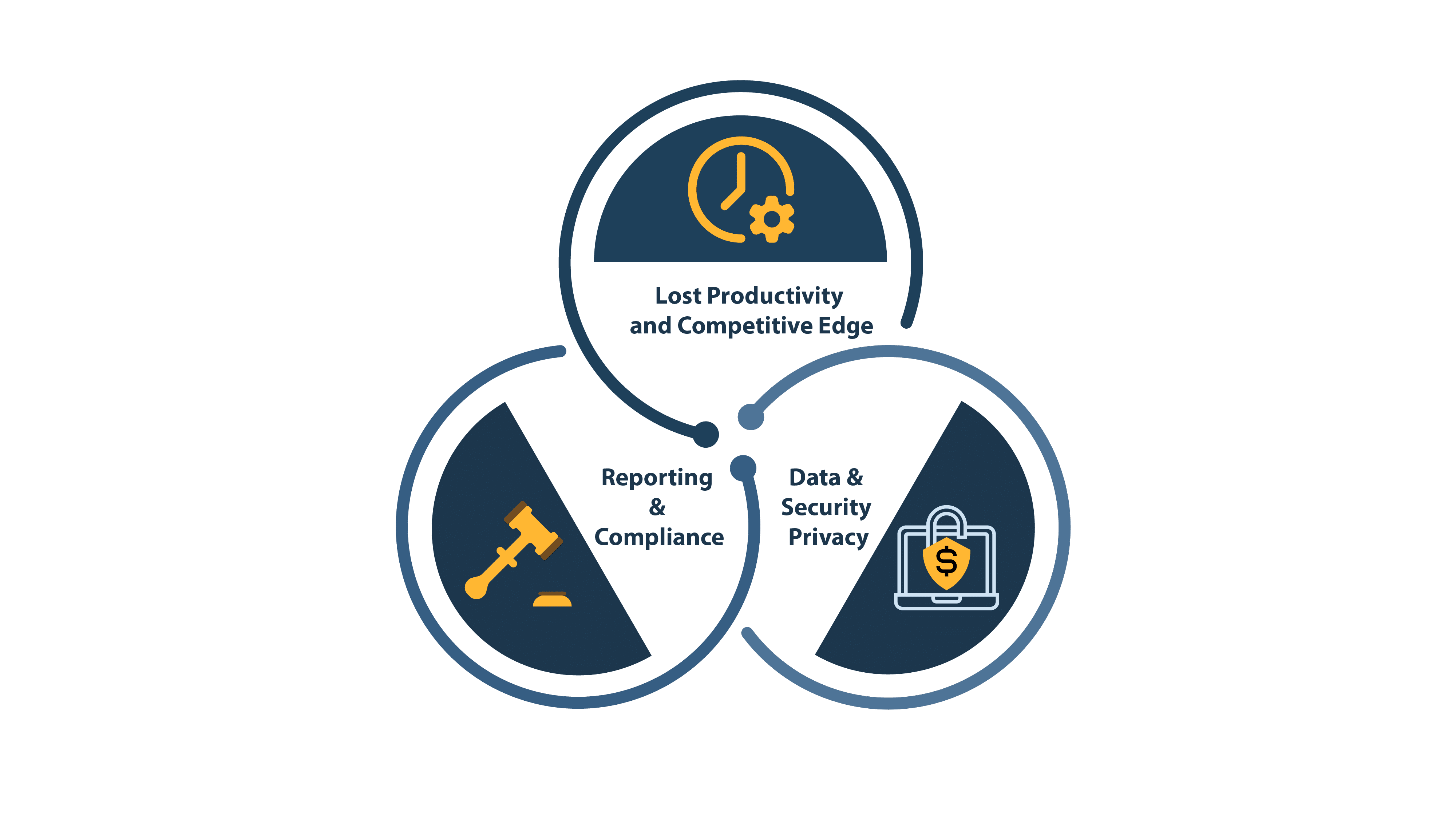
1. Data Security
This issue tops the list of interests. Cloud service providers are targets data destruction such as cloud based email delivering service like Send Grid, that makes important for the companies to use risk minimization strategies such as encrypting data before uploading it to the cloud. Use of local encryption and to adopt a cloud service provider who provides an necessary data encryption is an additional security layer.
2. Loss of Control
As per CSA survey 38% of IT leaders have worry over this parameter i.e. lack of control which keeps them from shifting data into cloud applications. It occurs when any client expend their limitation over their own data or resources in the hand of a service provider. This happens due to lack of access control and authentication placed by service providers.
The loss of control can be present in various ways. The service provider may favored exactly how and where data should be saved, how many time the backup should be taken, which encryption system should be used, which employees have the physical and logical access to the data.
3. Insider threats
Cloud services have broadly extended the scope of insider threat. Accidental data leakage is an important aspect of this. A user could also put a critical data in a publicly attainable location without intent, with just one click and our security efforts could be worthless. Another cloud associated insider risks are: the insider who utilizes a cloud related infirmity to steal information from cloud system, and the insider who makes use of cloud system to carry out a strike on employer’s local resources.
4. Business continuity and Disaster Recovery
Just imagine if a company loses all access to its IT Architecture due to its cloud provider has quickly stop operating? It’s a rare case, but still to maintain business continuity, recover the lost data and finding an appropriate alternative for that data can be a big challenge. To take the backup of the information is not only enough solution. There are few ways by which you can avoid data disaster such as:
1. Do work with trusted partners
2. Ensure that data is encrypted
3. Follow the rule of 3, 2, 1: Three copies of data that stored on two different types of media with any one of them stored offsite.
4. Apply 80/20 rule: Know your high value sensible data, which sections they arrange with etc. By applying this rule, company can easily taken out crucial data and applications which helps to decide which 20 percent is the most critical to protect.
5. Legal Issues: With collectively increasing laws on data protection , from General Data Protection Regulation (GDPR) law in EU on data protection and privacy for all citizens to Health Insurance Portability & Accountability act (HIPAA) in healthcare, to stay conforming with the laws is more difficult. For that companies must have dedicated governing rules that can enter which data to be accessed and what they can do with it. With the cloud feature of easy way to data, it can be difficult to keep track of who can access this data.
Issues can be appearing due to a selection of multiple service providers for parts of an overall solution. This creates a Virtual Machine (VM) packed with different agents, developing complexity and cut down the manageability. Solution to such issue is just finding out those few providers who have a strong approach to dealing with all such aspects.
What are the benefits of cloud computing system?
1. Protects your business from threats
2. Protecting against Internal Threats
3. Preventing data loss.
Top threats to the system include
1. Ransom ware and Malware breaches:
Near about 90% of malware comes through email. It happens frequently that user download malware without realising it. Once it gets downloaded, malicious software installs itself on our network which may cause loss content and remove files.
Ransom ware is another form of malware that seize our data and demands a financial pay-off. Now many cloud data security solutions identifies ransom ware and Malware and keeps malicious emails out of the user’s inbox. Spam filters, firewalls are examples of such Integrity management.
2. DDos Attacks and Protection:
Distributed Denial of Service attack occurs when system is flooded with multiple requests. Due to this our website becomes slow while loading until it crashes, if there are number of requests to handle.
DDos Attack is come up with important side effect on companies. Due to this attack, your website may unavailable after every minute. Some of the companies that experience DDos Attack lose near about $10,000 to $100,000. If critical data of customer is wasted in DDos Attack, then you may face a legal change. Many businesses experience reputation loss when customers lose their trust.
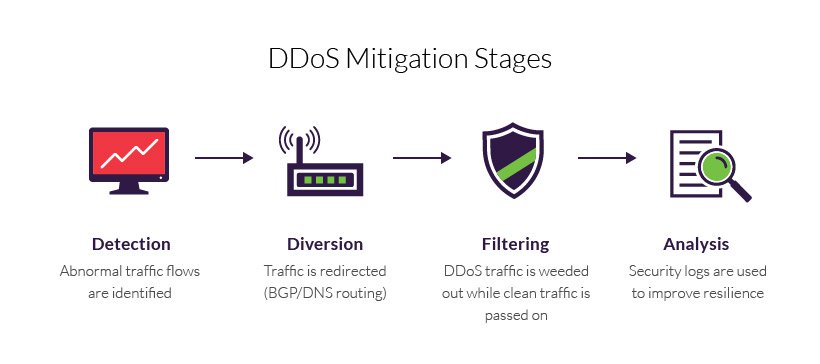
DDos Mitigation is the process of preventing targeted network from DDos Attack. This can be accomplished by employing specially designed network equipment so that attacked victim will be able to mitigate the incoming threat.
As IoT generates huge amount of data, cloud provides a runway to that data to travel. Cloud computing and IoT both enlarges to raise efficiency in everyday activities and they have an approving relationship. hIoTron Internet Of Things course will provide you a Technical expertise in Cloud Computing with live use cases using various IoT Cloud Platforms such as AWS, Microsoft Azure, etc. to learn in a more efficient way. Be a part of fastest evolving industry and Begin your journey into the IoT!